Сryptography is a complex science based on information protection. Most of the contemporary internet services such as internet banking, private messaging and personal data protection would not be possible without modern cryptography. A lot of today’s blockchain projects use additional cryptographic solutions, but most of them are not quantum-resistant. However, there are several projects, for example, GEO Protocol, which are already using post-quantum cryptography as the base technology to protect the data.
Computer cryptography
The most commonly used encryption methods initially were symmetric algorithms based on quite simple principles. Let’s say Alice and Bob need to exchange messages in a way that ensures no one else can read their contents when intercepted. For this purpose, Alice and Bob have a common secret key (a cipher). Using that secret key, Bob could encrypt a message and transmit it to Alice. Alice, in turn, could use the very same secret key on her side to decrypt the received message and read its contents. Backward communication from Alice to Bob will proceed in the same way.
Despite the simplicity and speed of these types of algorithms, they possess a number of serious drawbacks. The main problem is the need to have a secure way to pass the common secret key to the participants. In theory, Alice and Bob could meet in person and pass the key. However, if they would like to exchange messages with a large number of counterparts, or if they are located a long distance from one another, this way would not work. The most prominent symmetric algorithms today are Advanced Encryption Standard (AES), Data Encryption Standard (DES), International Data Encryption Algorithm (IDEA) and World AutoKey Encryption Algorithm. In 1975, as a response to the need for more advanced encryption methods, the concept of asymmetric encryption was introduced.
Let’s go back to Alice and Bob. Each of them has their own secret key, also known as a private key because no one should know this key except for its owner. And there is also a single possible open public key for every private key that can be made known to anyone. This pair of keys work in such a way that the public key can only be used for message encryption, but not decryption. In order to decrypt the message encrypted with a public key, you need the corresponding private key. If Bob would like to send a message to Alice, he takes her public key (that is freely available on the open network), encrypts the message and sends it. Alice is able to decrypt it with her private key, known to her exclusively, without fear that the contents of the message could be exposed to third parties.

How asymmetric encryption works
Cryptography in blockchain
Cryptography is at the heart of any blockchain, providing the basic functionality of the system. Blockchain architecture implies that the trust between the network participants is based on the principles of math and economics, i.e. formalized. Cryptography also guarantees safety, based on transparency and verifiability of all operations, in contrast to the industry’s traditional approach of limited visibility of the system’s critical parts (perimeter security).
The hash function is the cryptography basis of most existing cryptocurrencies. It can map input data of an arbitrary size to data of a fixed size, i.e. convert a random length data array to a bit string of fixed length. This operation is irreversible: in other words, in the function f(x)=y, we can find y if we know x, but we are unable to find x by knowing y. In Bitcoin, the role of such a function is performed by SHA-256. Another important feature of hash functions is the fact that even the smallest change of input data will result in a drastic change of hash. Thus the hash functions application in blockchain is to guarantee the integrity of the whole chain of transactions. Every new transaction block refers to the hash of the previous block in the ledger. The hash of that previous block depends on all past transactions in the block, but instead of consequently passing the hash from one transaction to the next, all of the hash functions are fused into a single hash line of the most recent transaction with the help of a binary hash tree (Merkle tree).

The Merkle tree
By using the hash function, you can express the general state of a blockchain — i.e. all previously performed transactions and their order — with a single line which is the hash of the most recent block. So, the immutability of any block’s hash guarantees the immutability of the whole blockchain.
The quantum threat
Quantum computers are computational machines of a fundamentally new level, significantly surpassing existing ones in terms of computing power.

IBM 50 qubits quantum computer
In traditional computing, a unit of information processing is a bit. Every bit can only be in one of two possible states: 0 or 1. In quantum devices, qubits (quantum bits) are used instead of bits. The main difference from bits is the ability for them to be in the state of 1, 0, and also in the state of 1 and 0 simultaneously (superposition).
In classical computations, only one of the 2^n data variants is loaded in the computer’s memory. So, only one of a possible 2^n data sets is processed at a time. However, in the quantum computer’s memory, all 2^n combinations of initial data is present and processed simultaneously. That means that the function for all possible 2^n variants of a data set is calculated during one operation (at the end, only one solution will be obtained). This way the computing power of quantum devices will help to obtain a private key using Shor’s algorithm (lowering resistance and applying new calculation methods).
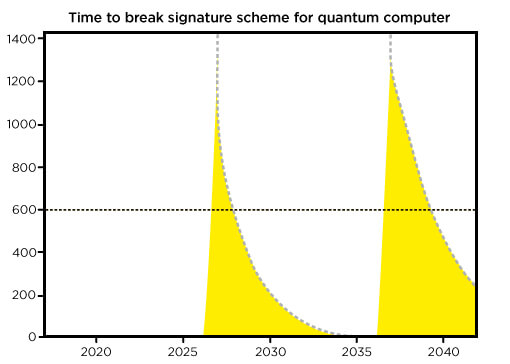
Two estimates of the time (in seconds) required for a quantum computer to break the signature scheme as a function of time.
Today there are just a few primary ways that provide protection from quantum computer attacks:
- Hash-based cryptography
- Code-based cryptography
- Multivariate cryptography
- Supersingular elliptic curve isogeny cryptography
- Symmetric key quantum resistance
- Lattice-based cryptography
Having long enough keys and following security requirements, these methods can resist both classic attacks and quantum attacks. Unfortunately, because of technical difficulty and the large size of quantum-resistant signatures, existent solutions can’t match the forthcoming threat. That’s why the developers of Bitcoin, Ethereum, NEO are seeking ways to solve this problem. But there are several projects, for example, GEO Protocol, that are already using post-quantum cryptography as the base technology to protect their data.
GEO Protocol
A unique feature of the GEO Protocol is that it is not based on a common ledger and is blockchain agnostic. That allows it to connect various blockchains, as well as non-blockchain-based assets. Transactions are performed by local off-chain consensus of the participating nodes only. All data is stored by the nodes, between which composite channels (a combination of state channels and trustlines) are installed.
On GEO network, every node stores its current balances and credit relationships with all neighboring nodes. This peculiarity of the protocol, along with the lack of a common distributed ledger (GEO is a non-blockchain solution), enables us to use one of the best ways to solve the quantum problem — the Lamport signature. The essence of this method lies in using one-time keys for each transaction. Keys are generated in advance and in limited quantity. After all the pre-generated keys are used, the new keys will be generated. This enables us to conduct an unlimited quantity of transactions securely and quickly.
Conclusion
The quantum threat feels like it’s a long way off, which is why most cryptocurrency projects don’t seem to care about it. The quantum threat is rarely discussed at blockchain-related conferences. But in the near future, that could all change, with a long-awaited quantum computing breakthrough rendering current encryption methods obsolete. Given this possibility, and the dangers it presents, the community should remain vigilant and take preemptive measures to counter this threat.